Authentication vs Authorization
Terminology
- Authentication (tokens)
- The process of verifying who a user is.
- Authorization (access tokens, keys)
- The process of verifying what an application has access to.
Comparing these processes to a real-world example, when you go through security in an airport, you show your ID to authenticate your identity. Then, when you arrive at the gate, you present your boarding pass to the flight attendant, so they can authorize you to board your flight and allow access to the plane.
Source: - Authentication vs. Authorization on Auth0
Common API connection methods
Note: Basic Authentication (when you type your username and password) is not recommended for API connections.
API Keys
- Is an authorization scheme that does not authenticate the user.
- Identifies the application making the request and can be revoked.
- Keys are considered public and are inherently insecure.
- The general process for creating a key:
- Login to the service portal.
- Find/generate your API key. This is usually under Settings or similar.
- Copy your API key into your application.
- Follow the instructions provided by the service to test your API key.
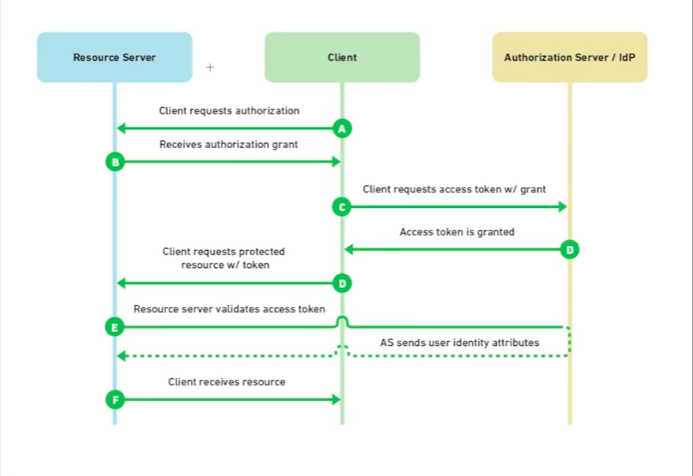
OAuth2 Tokens
- A modern (and often recommended) authentication standard that identifies the user to a service (i.e GitHub, Twitter, etc).
- Tokens should be kept private and should only be used on the server, never the browser.
- Access tokens can be tied to particular scopes, which restrict the types of operations and data the application can access.
- Like API keys, tokens can be revoked.
JSON Web Tokens (JWT)
- JWTs can be used for other purposes than API authentication.
- Is a token scheme that can be used in combination with OAuth.
- Advantage: a JWT can store any type of data, thereby reducing the number of database calls.

